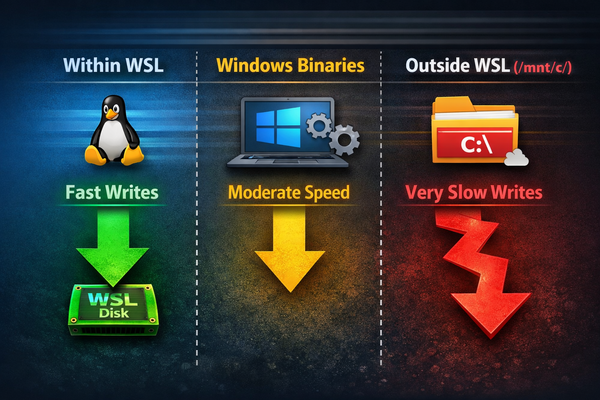
When people ask what their baseline configuration should be, in terms of logging, I feel like it often gets answered with general advice regarding knowing your environment, having different configurations for file servers vs domain controllers, etc. This is true advice, but not particularly helpful. You might not know your