Encrypted Data Communication: An Overview of the WEP Standard
This paper was written several years ago as part of an undergraduate class. I don't think it's the best in the world, but I was told it was good enough, and accurate enough, that it should go on a blog should I ever make one. So here it is. Please feel free to correct any inaccuracies in the comments.
---------------------------------------
Wired Equivalent Privacy, or WEP, is a security algorithm produced by the IEEE as part of the 802.11 standard. This paper will give an overview of this standard, beginning with the history and its implementation, the technologies that make up WEP, how it works, and some of the security flaws inherit in the design.
WEP was introduced as the first security standard available to wireless networks in 1999. The goals of this standard were not to provide unbreakable encryption, but rather to make it difficult to crack. The IEEE also had to keep in mind the available hardware at the time of development. Access points simply did not have the processing power they do today and needed to be able to decrypt traffic in real time. They defined five objectives as part of this standard (“Chapter 6”): WEP needed to be reasonably strong, self‐synchronizing, efficient, optional to implement, and exportable (useable in other countries and regions). Initially, it met every one of these goals. However, in 2001, a severe flaw in the standard was published (Fluhrer et al.). Since then several other flaws have been demonstrated (Bittau et al., Tews et al.), automated tools have been created, and attacks have been refined. As of 2010 WEP is considered so insecure that the Payment Card Industry prohibits the use of WEP as any part of credit card processing (“Information Supplement”). Today a WEP protected network with a high volume of traffic can be accessed by a third party in a matter of minutes (Cheung), if not seconds. Despite these serious shortcomings, about a quarter of wireless networks still use WEP encryption, or worse, no encryption at all. (Botezatu)
Several different technologies are used in WEP, it is important to know what these are in order to understand the encryption process. They include the Integrity Check Value (ICV), which is a CRC‐32 checksum, the 24‐bit Initialization Vector (IV), and the Rivest Cipher 4 (RC4) cipher used to encrypt the data (Chandra). The checksum is used to verify the integrity of the data in the original message. The IV is, ideally a random number that is used in combination with the shared key (the password set in the access point in this case) to seed the RC4 encryption. The idea behind this is to keep the seed from being constant, thus making the encryption more secure (Rouse). Finally, the RC4 encryption, which is one of the most widely used stream ciphers because of how quickly it can be encrypted and decrypted ("RC4."). It is important to also have a basic understanding of exclusive or (XOR) ciphers. A simple explanation is that it is an additive cipher; one takes a message, adds a key to encrypt it, and when the recipient receives the message the key is subtracted and the message remains. Without knowing what value to subtract for the key, there is no way to decrypt the message (Rick). WEP technology and history have now been explained, but not how it actually works. This is explained using a simplified example, but it is best understood using the visual provided below (Chandra).
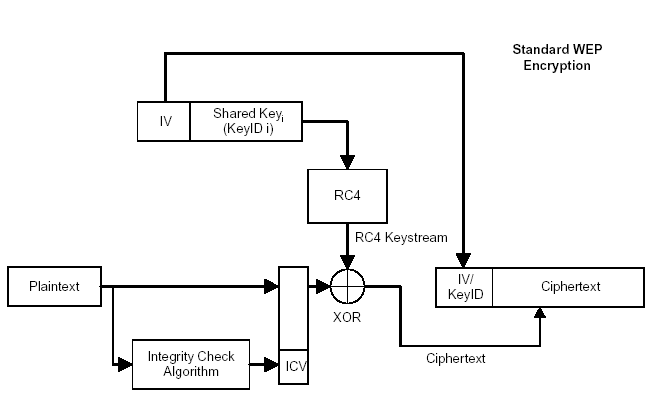
First, the computer takes the message to be sent, for demonstration purposes the string will be “Newcastle”, and appends the CRC32 value to yield “Newcastle:b54dd1ca”. This is the plain text package the computer wants to send (PT). The computer encrypts that package using RC4. In WEP RC4 uses two inputs to generate a key stream. These inputs are the shared password and the IV discussed above. This key stream is then XORed with the plain text package to produce an encrypted package (Epackage). The IV is then prepended to the front of the Epackage (it is important to note that the IV has NOT been encrypted) and sent. When the access point receives this, it reads the IV, strips it from the Epackage, uses the IV and the shared password to run the algorithm in reverse (decrypts the package), checks the message against the checksum, and if the message is intact, passes it along.
There are a few things to note. Remember the initialization vector was used to keep the RC4 seed from being static every time. If the same information is encrypted with the same key every time, eventually the encryption would become predictable and even loop around to the start. This is a definite possibility when encrypting and sending gigabytes of data. To have an effective stream cipher, the same key should never be used twice, hence the IVs. However, a 24‐bit IV only provides about 16 million possibilities. On a busy network this would only take a few hours to exhaust, but in practice an IV usually gets reused every 10,000 packets. This is the first flaw in WEP, the short IVs causing then to be reused. The second flaw is that this IV is transmitted in plain text! This means it is know exactly which two messages were encrypted with the same keystream, since the keystream is made up of the static shared password and the IV. All that is needed to completely break the encryption is two packets that use the same IV.
It is important to note exactly how WEP might be broken, again using a simple example. A few thousand packets are collected by a wireless monitor. Among these packets are two that share the same IV. Most packets share a value called a SNAP header(2*), since this value is known and the cipher text (CT) version of it has been captured, a plain text and cipher text pair (PT1 and CT1) are now known. It is also known that these were encrypted with a key that will be designated Key A (using IV A). Now take the second packet, which also uses Key A, the CT for this packet (CT2) is known, but not the plain text (PT2) value. Key A can be used to decrypt it, revealing PT2 (Doraiswamy).
Eventually, even if the shared password is never discovered, this method can be used to gather every key used and decrypt any message sent over the network. However, it is also possible to uncover the actual shared key (password). If an abstract example is used, the encryption can be thought of as an algebra problem. It is known that KeyA = X+IVA and that (X+IVA)+PT1=CT1, also that (X+IVA)+PT2=CT2, therefore X=(CT‐PT)‐IVA. The unknowns CT and PT can be determined because two different examples of each are available. Once this is done it becomes easy to solve for X, which is the shared password. The computational process is much more difficult and complex than the example above, but with automated tools and modern processors a computer can find the answer in seconds given the right information.
Given these flaws, two questions may spring to mind, how do people secure their networks, and why do people continue to use WEP? In answer to the first question, IEEE has created several alternatives, the most recommended one is the WPA standard created in 2003 and WPA2 created in 2004. There were also several enhancements created for WEP to create more secure networks until better methods could be created, such as WEP2, WEP+ and Dynamic WEP. WEP2 was designed to create stronger IVs and keys and to prevent brute force attacks, however, the overall design of WEP was still flawed and this method was dropped. WEP+ simply avoids “weak IVs”, IVs that expose more information than they statistically should. This only makes breaking the encryption slightly more difficult, it does not truly solve the inherent problem. Dynamic WEP changes keys continuously, and although this provided the best protection, there are still underlying problems with WEP. None of these standards were ever adopted by mainstream manufacturers, either because they were vender specific or proprietary features, or it was determined they were still too insecure to become the next encryption standard. MAC filtering can also be used to try to limit network access, but this is vulnerable to its own set of attacks.
The history of the WEP encryption standard, the other technologies are infused into it, how it works, and the flaws inherent in that design have now been explored. This lead to questions about how these flaws can be exploited to gain access to a network and how to better secure wireless networks. While most of this information is unnecessary for end users, perhaps a broader knowledge will help eliminate the percent of unsecured/poorly secured networks in the wild.
Works Cited
- Bittau, Andrea, Mark Handley, and Joshua Lackey. "The Final Nail in WEP’s Coffin."Http://www0.cs.ucl.ac.uk. N.p., 2006. Web.
- Botezatu, Bogdan. "25 Percent of Wireless Networks Are Highly Vulnerable to Hacking Attacks, Wi‐Fi Security Survey Reveals." Http://www.hotforsecurity.com. N.p., 11 Oct. 2011. Web.
- Chandra, Praphul. "802.11 Security." Http://www.wirelessdevnet.com. N.p., 23 May 2002. Web.
- "Chapter 6. How IEEE 802.11 WEP Works and Why It Doesn't Introduction." Http://etutorials.org. N.p., n.d. Web.
- Cheung, Humphrey. "The Feds Can Own Your WLAN Too." Http://www.smallnetbuilder.com. N.p., 31 Mar. 2005. Web.
- Doraiswamy, Arvind. "Wireless Security ‐ Cracking WEP." Http://palpapers.plynt.com. N.p., Feb. 2007. Web.
- Fluhrer, Scott, Itsik Mantin, and Adi Shamir. "Weaknesses in the Key Scheduling Algorithm of RC4."Aboba.drizzlehosting.com. N.p., 2001. Web.
- "Information Supplement: PCI DSS Wireless Guideline." Https://www.pcisecuritystandards.org. Security Standards Council, July 2009. Web.
- "RC4." Http://www.princeton.edu. N.p., n.d. Web.
- Rick. "Stream Ciphers." Http://www.cryptosmith.com. N.p., n.d. Web.
- Rouse, Margaret. "Initialization Vector (IV)." Http://whatis.techtarget.com. N.p., Mar. 2011. Web.
- Tews, Erik, Ralf‐Phillip Weinmann, and Andrei Pyshkin. Http://eprint.iacr.org. N.p., 2007. Web.
