Proxying Non-browser Traffic Through Burp
Or "Microsoft SQL Express and the Truly Terrible, Just Awful, No Good Downloader"
TL;DR up front.
- On a secondary machine/VM, setup a Burp proxy to use the non-localhost interface (192.168.1.230 in my case) as a proxy. Turn off intercept
- On your Windows system, set Internet Properties to use that system (the IP we used above) as the proxy by going to Connections -> LAN settings -> Use a proxy server for your LAN.
- Install the Burp certificate as instructed here: https://portswigger.net/support/installing-burp-suites-ca-certificate-in-internet-explorer
- Profit: You should now be proxying everything Windows does through your secondary machine.
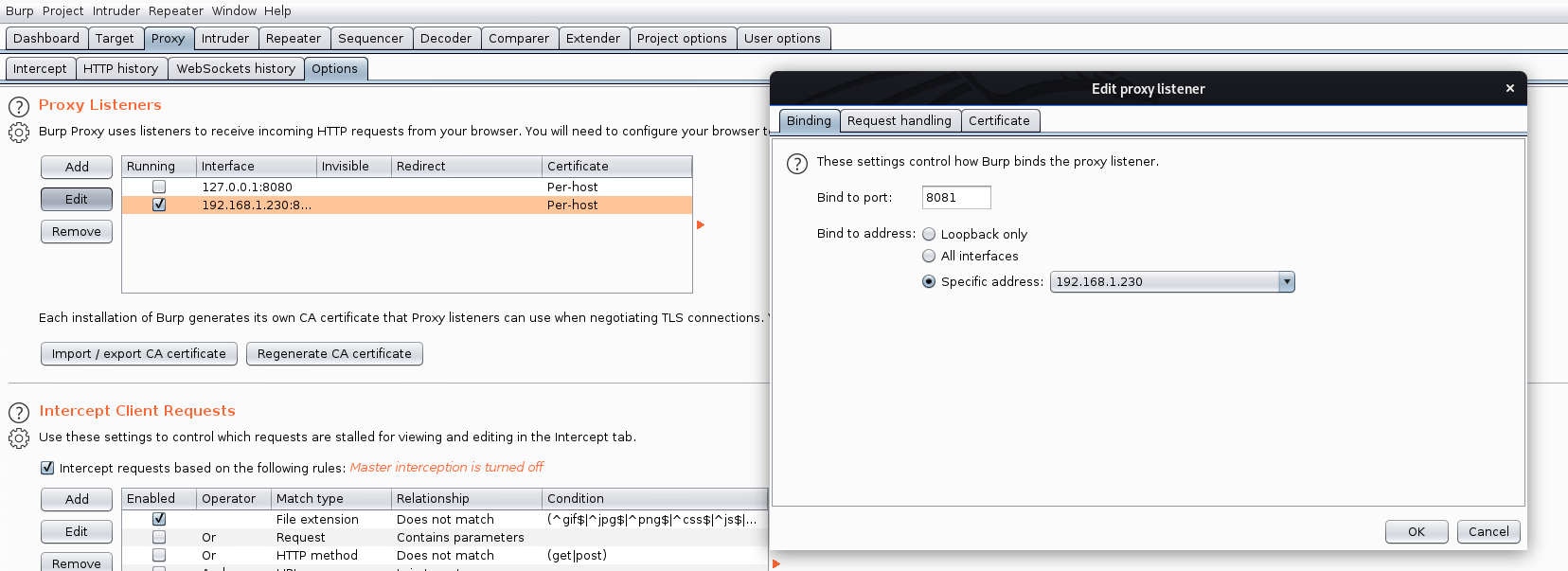
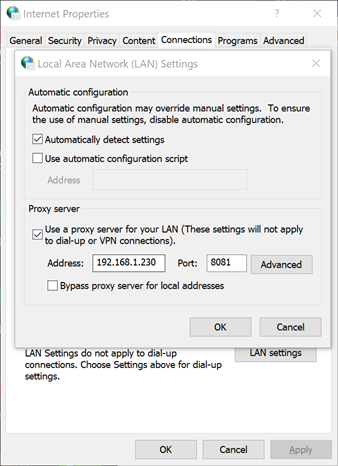
Now why would I want to do this? Because thin-client downloader things are a terrible idea! This started out with a test machine and my desire to install SQL Server 2019 Express. So you find the page, click Download under Express, and you get a ~5mb file. I run this, and I get an error:
Failed to execute activity MediaDownloadActivity
The SQL installer file "SQLEXPR_x64_ENU.exe" could not be downloaded. The following information might help resolve the problem:
Status: 'ReceiveFailure',
Description: 'The underlying connection was closed: An unexpected error occured on receive'
Some Googling told me to try "Download Media", but this resulted in the same error.
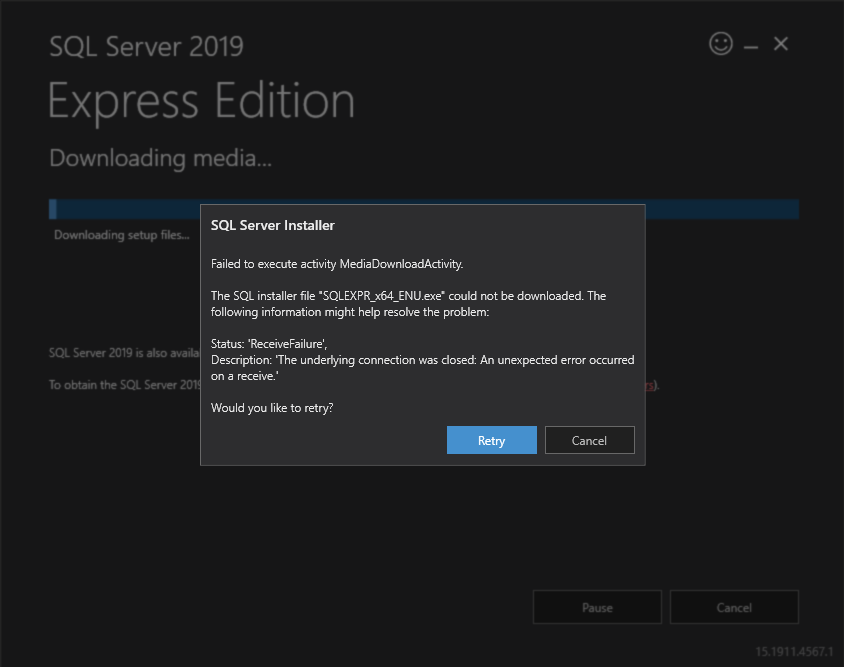
I have the feeling I know why this is failing. I hardened my server a bit with IISCrypto and disabled everything except TLS 1.2 (because we're in 2020), and all the Cipher Suites except ECDHE ones. I had a hunch that Microsoft's broken downloader can't handle newer protocols and/or cipher suites.
Being Microsoft, there is no link to just download an offline installer. Rather than admit defeat and change cipher suites back, I setup the proxy mentioned above, moved the downloader to my desktop (with slightly more permissive TLS settings), and fired it up. Right away I see the download begin.
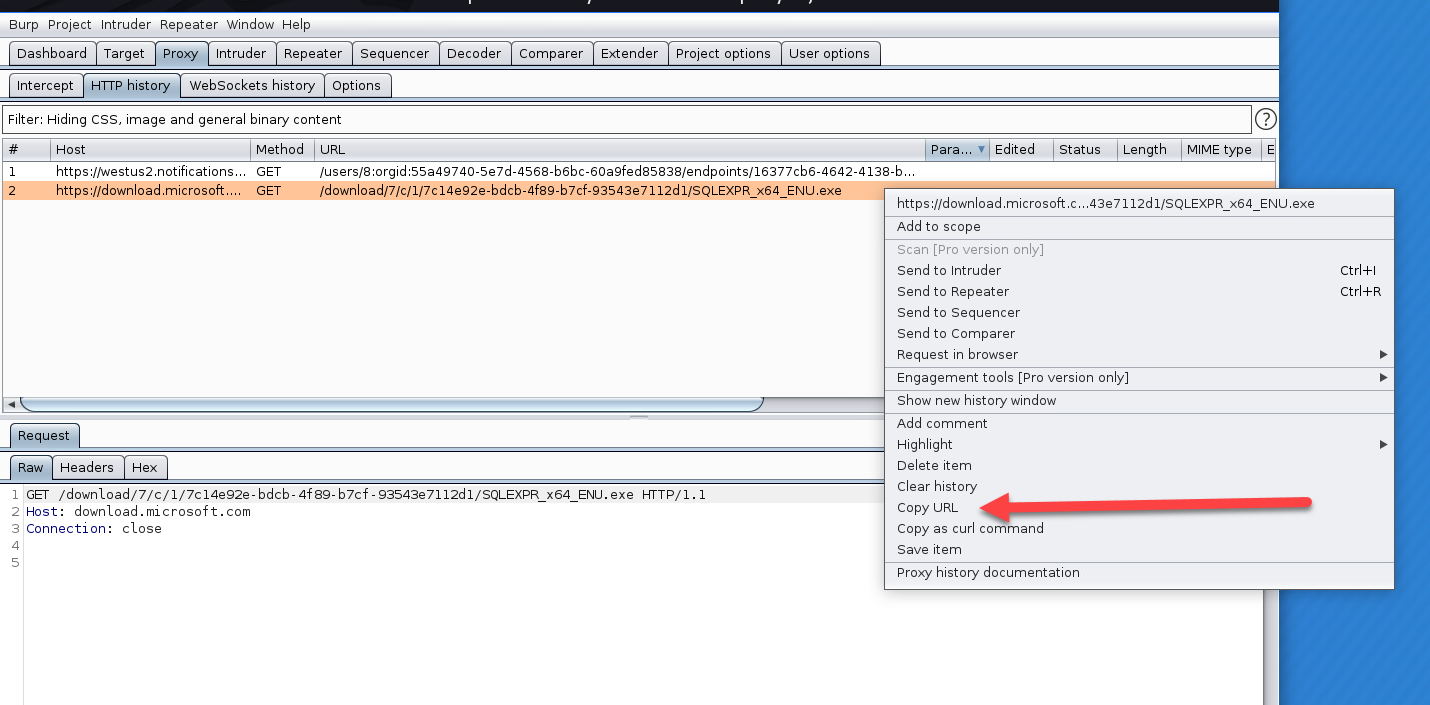
The resulting URL, https://download.microsoft.com/download/7/c/1/7c14e92e-bdcb-4f89-b7cf-93543e7112d1/SQLEXPR_x64_ENU.exe, will probably change when a new version is released, but has stayed stable for about a week now. Sure enough, if I paste that URL into IE (or any other browser) on my server, it works and downloads the full ~248mb version of SQL Express.
With my stubbornness satisfied, I wanted to prove that a) I was right, and b) What requirements were necessary to make the client work. It turns out that by enabling TLS 1.0 (that's right, the deprecated version) under "Client Protocols", you could make the downloader work (no cipher suite modifications necessary).
@microsoft (and anyone else that does this) - Stop hiding the full versions, and how is a brand new downloader branded with "2019" still requireing TLS 1.0?
Relevant Files/Checksums
Algorithm Hash Path
--------- ---- ----
SHA256 82FDECCBE3E3201D3889705BCA45DE587D3297DF97E7E74F21F8FA11DAD0A68F SQL2019-SSEI-Expr.exe
SHA256 BEA033E778048748EB1C87BF57597F7F5449B6A15BAC55DDC08263C57F7A1CA8 SQLEXPR_x64_ENU.exe
