Password Spraying SMB
TL;DR - I wanted to audit for the presence of a particular username, with a particular password, across every endpoint in our environment. As usual, I had a theory. The theory was that, when we applied LAPS several years ago, there were things that got missed (as their always are). I want to find those things, and remediate them.
Very briefly, because it's not the main point of this post, the way I found them was via masscan. It's amazing and I'll do an article on it shortly, but for now just know that it quickly (as in, ~5 mins) allows me to find every system listening on 445/TCP across roughly a /16. Nmap is nice, but not that quick. This narrowed 65k addresses down to ~5,000 that I knew were alive. masscan -p 445 --rate 4000 --open -iL <file with list of ranges>
From here I wanted to find the best way to check these credentials against the given list. Here are the options I found, let me know in the comments if you have any others.
- Metasploit auxilary/scanner/smb/smb_login
- CrackMapExec
- Medusa
- Ncrack
- Hydra
- Nmap smb-brute
Of these, Metasploit tops my list. Only it, and CrackMapExec seem to support SMB v2. Without this, my results seemed to return negative on a number of hosts that should have been positive (false negatives). Medusa and Ncrack do ok, but don't support this protocol. Hyrda I didn't like the format of, and Nmap smb-brute might work for other purposes, but didn't at all for mine. I'll go over these in reverse order below.
Nmap smb-brute
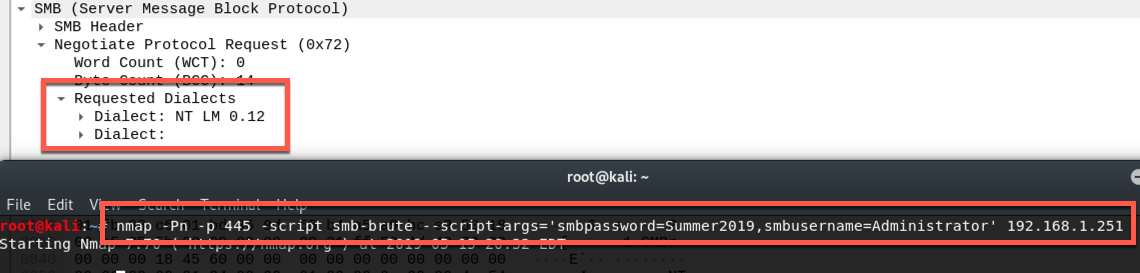
As I mentioned above, the lack of SMB v2 was a no go from the start. However, I was also never able to get this script to only test against my supplied credentials. Perhaps this is the way it was designed. If I'm supplying the wrong arguments, please let me know in the comments. However, it seemed to perform a brute force no matter what, which I didn't want for this use case. You can see below what I'm talking about as it tries various users from the built-in database.
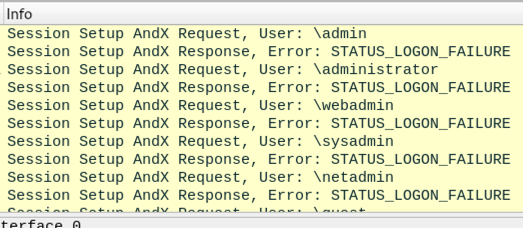
Requested Dialects: NT LM 0.12
Hydra
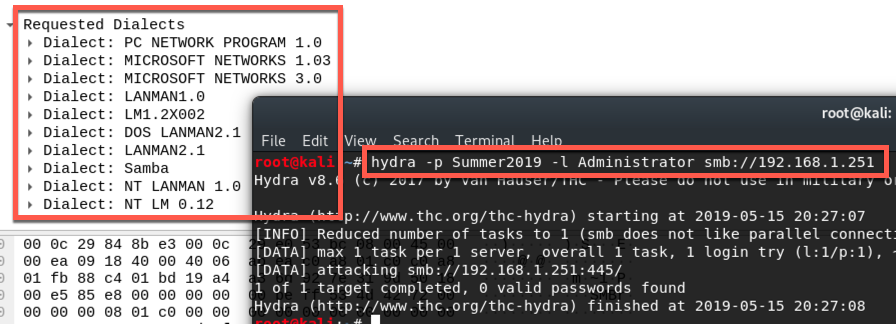
That list of dialects! but not an SMB in sight... There are times I like the protocol://host:port format that hydra uses. However, this isn't one of them since I eventually want to feed it a very large list. It would be better if I could specify the protocol seperately. I think there's a way to do this, but without SMB support, it was out of the race anyway.
Requested Dialects: PC Network Program 1.0, Microsoft Networks 1.03, Micrsoft Networks 3.0, LANMAN1.0. LM1.2X002, DOS LANMAN2.1, LANMAN2.1, Samba, NT LANMAN 1.0, NT LM 0.12.
Ncrack
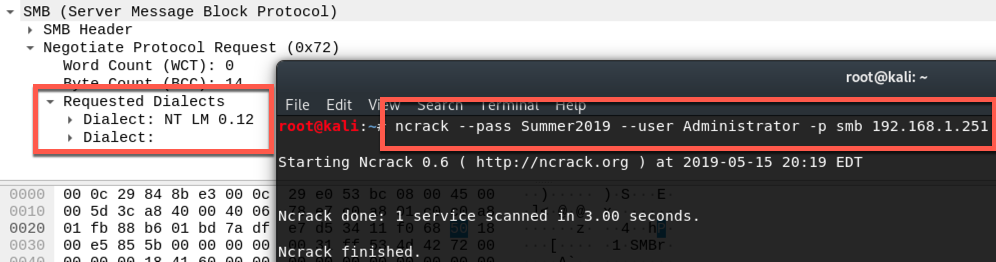
Ncrack works well enough, but doesn't have the dialects support I'm looking for.
Requested Dialects: NT LM 0.12
Medusa
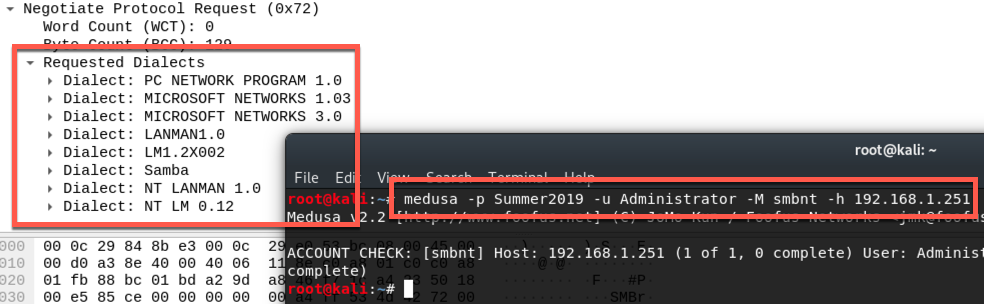
Much like Hydra, Medusa has a nice list of supported dialects, lacking DOS LANMAN2.1 and LANMAN2.1 compaired to Hydra. These two, and Ncrack, are usually my go to for password spraying against services.
Requested Dialects: PC Network Program 1.0, Microsoft Networks 1.03, Microsoft Networks 3.0, LANMAN1.0, LM1.2X002, Samba, NT LANMAN 1.0, NT LM 0.12.
CrackMapExec
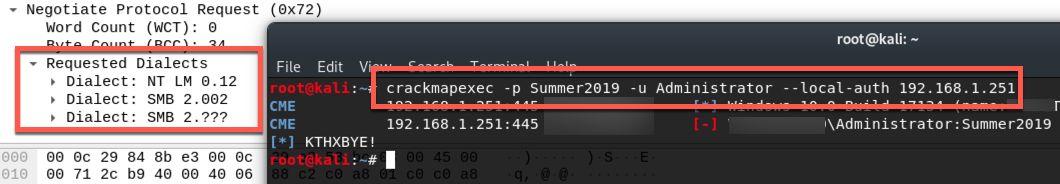
CrackMapExec is great, and it's what I originally went to with it's support for SMB seen above. However, I encounted a crash about ~1500 systems in. Adjusting the threads and other settings didn't seem to help. A colleague wasn't able to narrow this down to a specific host. I suspect something was returning a result that wasn't expected (not everything with 445 open was a valid Windows system that would return expected results). In any case, it works great, and I would suggest trying it if you're after the same thing. It also comes in a Windows version bundled with Commando VM if that OS is better suited for you.
Requested Dialects: NT LM 0.12, SMB 2.002, SMB 2.???
Metasploit
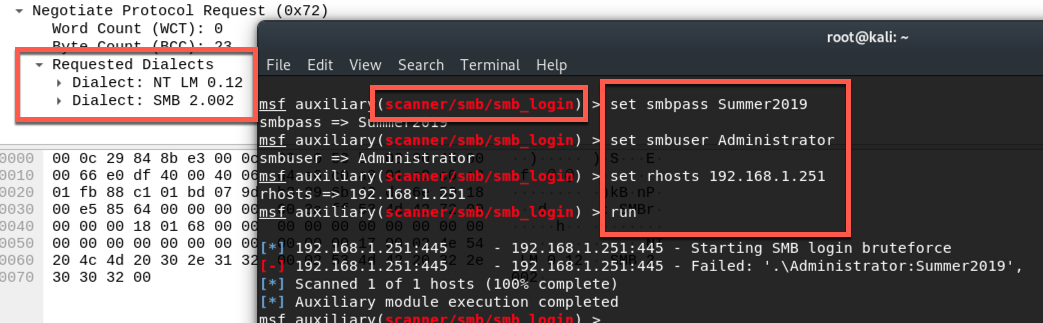
the smb_login auxilary module still returned a few errors and timed out on some hosts. However, instead of this terminating the scan early, it continued on. I did notice some false positives that I don't believe were related to the scanner, but in the way the endpoint would respond. Several systems seemed to return an Authentication Success message regardless of the username/password entered. These were pretty easy to weed out though by scanning for a set of credentials that couldn't possibly be valid.
One additional important thing I learned though this process is that Metasploits RHOSTS value can take a file as input! use: file:/directory/file.txt
My final results ended up looking like the screenshot below. I've highlighted the settings I've changed, the rest are default.
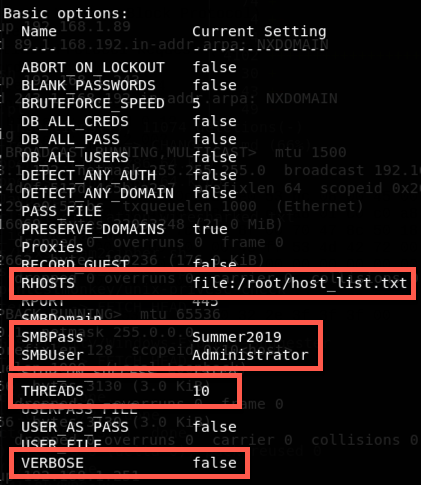
Supported Dialects: NT LM 0.12, SMB 2.002
