Integrating BeEF and Metasploit
This isn't exactly undocumented, but I definitely feel like it's underdocumented. I've seen the metasploit browser_autopwn feature in the modules in the past, but what I didn't realize until recently is that BeEF integrates directly with Metasploit. There's a lot more metasploit modules available.
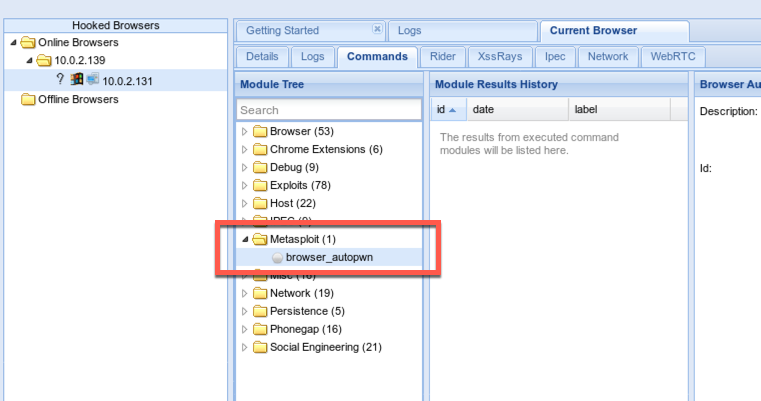
1) Enable the Metasploit module in BeEF's config
Open /usr/share/beef-xss/config.yaml and change metasploit under the "extension" category from false to true on about line 155/156 (in my updated version of Kali).
# You may override default extension configuration parameters here
extension:
[...snip...]
metasploit:
enable: true
2) Enable the Metasploit module in BeEF's config
Yes, I just repeated myself. There's another configuration file in /usr/share/beef-xss/extensions/metasploit/config.yaml. In theory you can change any of the options (username, password, port, SSL, etc.). In practice, I've found that the metasploit modules don't populate in beef if anything is changed. Just set the enabled value to true and leave the rest of it.
beef:
extension:
metasploit:
name: 'Metasploit'
enable: true
host: "127.0.0.1"
If anyone knows why changing any options breaks things, please leave a comment.
3) Start the metasploit service
Start msfconsole and then load the msgrpc service.
msf > load msgrpc ServerHost=127.0.0.1 Pass=msf
The other optional values that you -should- be able to set are User=<value>, SSL=y, and ServerPort=<value>. Note that these values, and those above, are case sensitive.
4) Start beef
start-xss
Or see: GHOST_URL/kali-running-beef-xss-on-port-80/
5) Profit
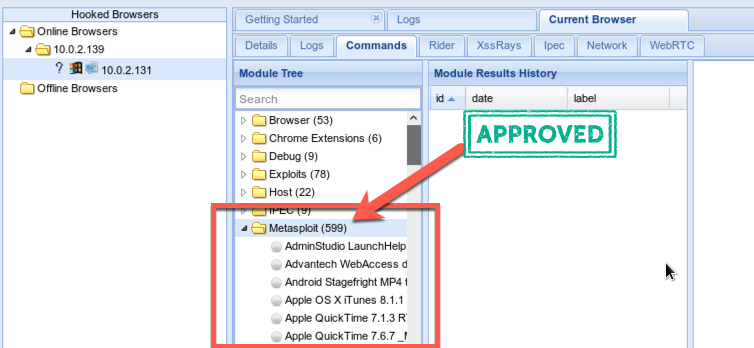
599 modules! Winning!
Other Resources:
