Examining SMS Phishing
I received a phishing message via SMS today directing me to hxxps://cutt[.]ly/WegUqPxy?Lgp=brg1CtzWGg. I haven't done a post in a while, and thought this might be interesting to examine.
urlscan.io
This is a great site for examine single page phishing or suspect sites. Putting that cutt.ly link into urlscan.io gives me this result: https://urlscan.io/result/b2f1b71e-a789-4743-85c9-f26b6f7e67f3/#summary
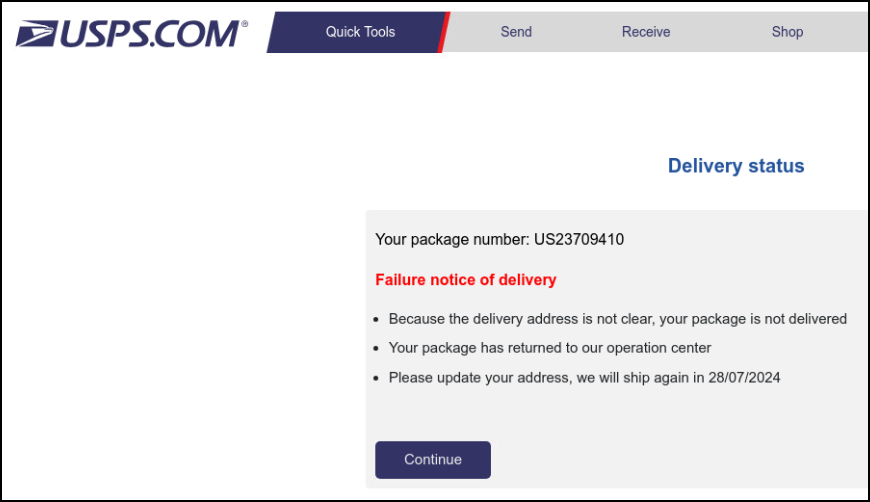
One thing we see right away is that we get a 404 page back. A lot of people might be tempted to think that means the phishing page was taken down, and that may be the intent of the threat actor here. However, we see something completely different if we set custom options. Specifically the Custom User Agent field, which I set to a mobile device user agent, Mozilla/5.0 (Linux; Android 13; Pixel 7 XL) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/122.0.0.0 Mobile Safari/537.36 as would be expected from an SMS message. Now we get back something that is very clearly a USPS phishing page that lands on hxxps://usjc.rqchryeg[.]top/813d59/EAA8Ad2nZAqesv1AJVHAww4uJAA_LH/X3VMqdA9GIdAP4fPyfiyCuiHt95EAsAAbuNA/yqJP?9
https://urlscan.io/result/bc03b2e6-f746-4450-bd64-b7620a767d45/#summary
There's a lot of other good info here. We can see that this is hosted behind CloudFlare in the Domain & IP information at the bottom. If we go to the Redirects tab we can follow the HTTP requests that we got to get from cutt.ly to rqchryeg.top. Links, Indicators, and other tabs may be of interest to defenders, and of course there's a screenshot of the page itself.
We can also see this page and interact with it using something like User-Agent Switcher and setting a mobile client. Something interesting to note, which you can see in the Links section on urlscan but is even easier to notice on the live site, is that all of the links do go to their proper usps.com page:
Walking Through the Form
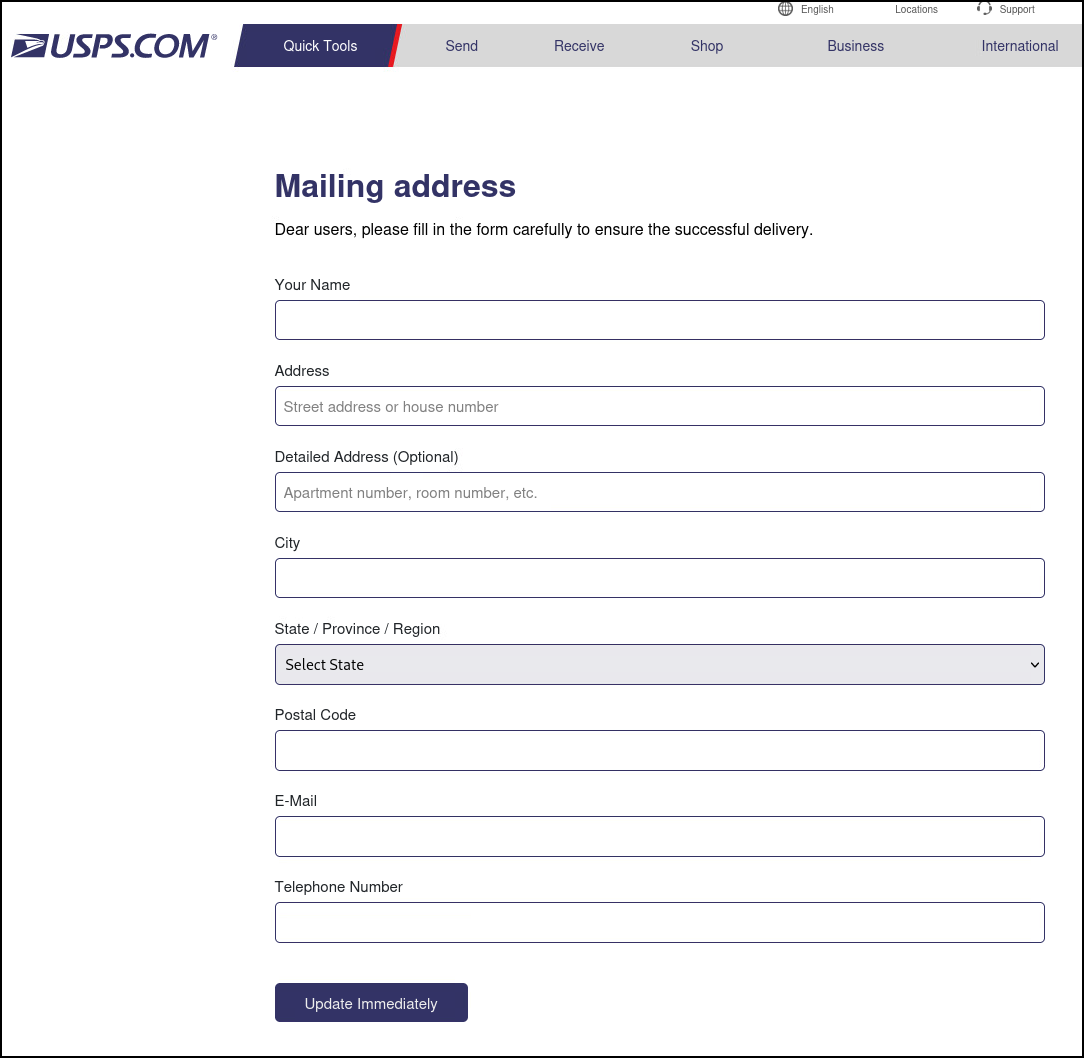
While we are here, lets click "Continue" and see where this form takes us. Right away we get a new page asking for our updated delivery information. I'm going to use Fake Name Generator to give it something false, but realistic looking.
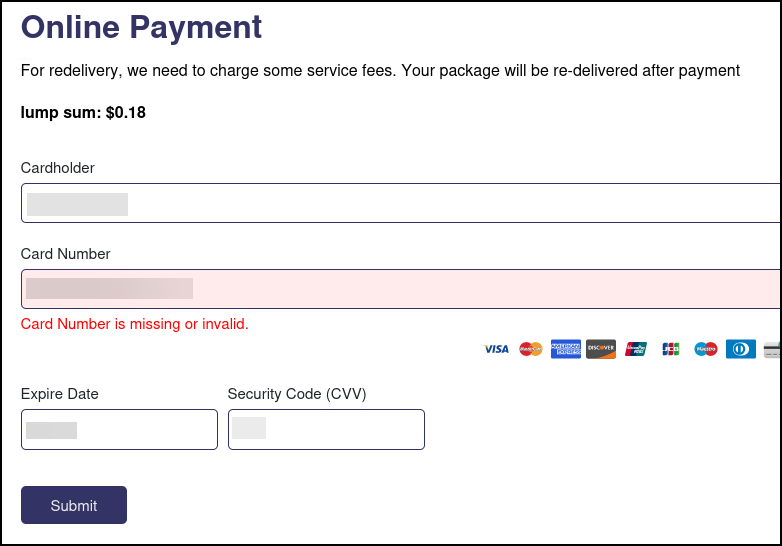
After clicking Update Immediately, I get to what the TA is really after, credit card information, so they can process my 18 cent redeliver fee.
Once again I gave it fake information, which was returned with an error this time. I'm not sure if this is because they are actually validating card information somehow, or if it would always return an error, possibly prompting someone to try a different card.
Domain Tools
Another service that I like for checking up on these sites is Domain Tools. This particular one can be found here: https://whois.domaintools.com/rqchryeg.top There isn't a lot in this one, but one thing I always check is the registration date. In this case, it was 36 days prior to the publishing of this article. This kind of information might tell me if it was something setup by the threat actor, or if it's a compromised victim. In this case, just over a month old tells me that it's probably something setup specifically for this activity. If it was a 10 year old domain, it may be a legitimate site that was compromised and is being used as a host. In that case, I might try finding the owners of the site.
Sometimes you'll find other goodies in here, for example if the registration information isn't redacted. For older sites, you can also view the registration history (with a subscription) which may include contact information prior to redaction, old IP addresses prior to it being placed behind a CDN, etc.
Krebs did a very recent article on these .top domains: https://krebsonsecurity.com/2024/07/phish-friendly-domain-registry-top-put-on-notice/
Shodan / Censys
At the time of this post, neither Shodan nor Censys had anything to show for rqchryeg.top, but they are also good places to check.
Interesting Pages
Going back to browsing around the site and trying a few common things, I did notice that by going to /admin, you get redirected to a blank/empty page at Admin/Home/Login https://urlscan.io/result/34caef5f-0997-4d8c-af97-0ffabb2d8e3d/#behaviour
A few other pages also give you an HTTP 403 (Forbidden) page, rather than the 404 not found. These include /content, /log, /scripts, /upload, /assets, and /plugins (that I found, I'm sure there are more). This tells me that there may be something there. It may also be interesting that I noticed a few things, like /img, that returned a valid 200 status code, but text on the page that said Error:403. It looks like this may be handled by ASPX based on the redirect to /StaticHtml/UpdateHtml/index.html?aspxerrorpath=/img. There were a number of other pages/files like this.
I didn't find anything here, but I have more than once seen threat actors leave their control panel wide open on compromised infrastructure. I've found C99 web panels with no credentials set and a very organized set of folders detailing several dozen large organizations they were attempting to phish, with all the results stored in plaintext.
If anyone knows what toolkit is being used here based on some of the results, I'd love to hear what you know.
Recon Tools
Taking this to the next step, you can explore the site using typical recon tools. dirb, gobuster, and nmap to name a few. Doing so moves you from passive OSINT into more of a grey area though. I view enumeration tools like Nmap and dirb (where they are only enumerating, and not password spraying or other plugins) as perfectly reasonable to use against any site, just be polite with your rate. They aren't doing anything that I couldn't do by hand, and are only returning publicly available information that anyone could view. However, I've had more than one debate about where the line is crossed when it comes to pentesting and similar activities. Remember, you always need permission. Therefore, I won't be covering that here.
Wrapping up
I can't think of anything else to explore here. Since this is recent TA infrastructure, there isn't a lot of history, potentially open services, additional pages, or other threads to pull that you might see on compromised infrastructure.
Like I said above, if anyone knows what toolkit might be used to host this, I'd love to know. I'm fairly sure the values in the URL's are used to track campaigns somehow, and it would be interesting to know if we can modify them to find others. It would also be interesting to know if there are any admin panels we can reach.
