EventFinder2 - Finding Events by Time
TL,DR upfront - I created a small program to grab all event logs between a beginning and end time mark and write them to a CSV. Find it here: https://github.com/BeanBagKing/EventFinder2
About
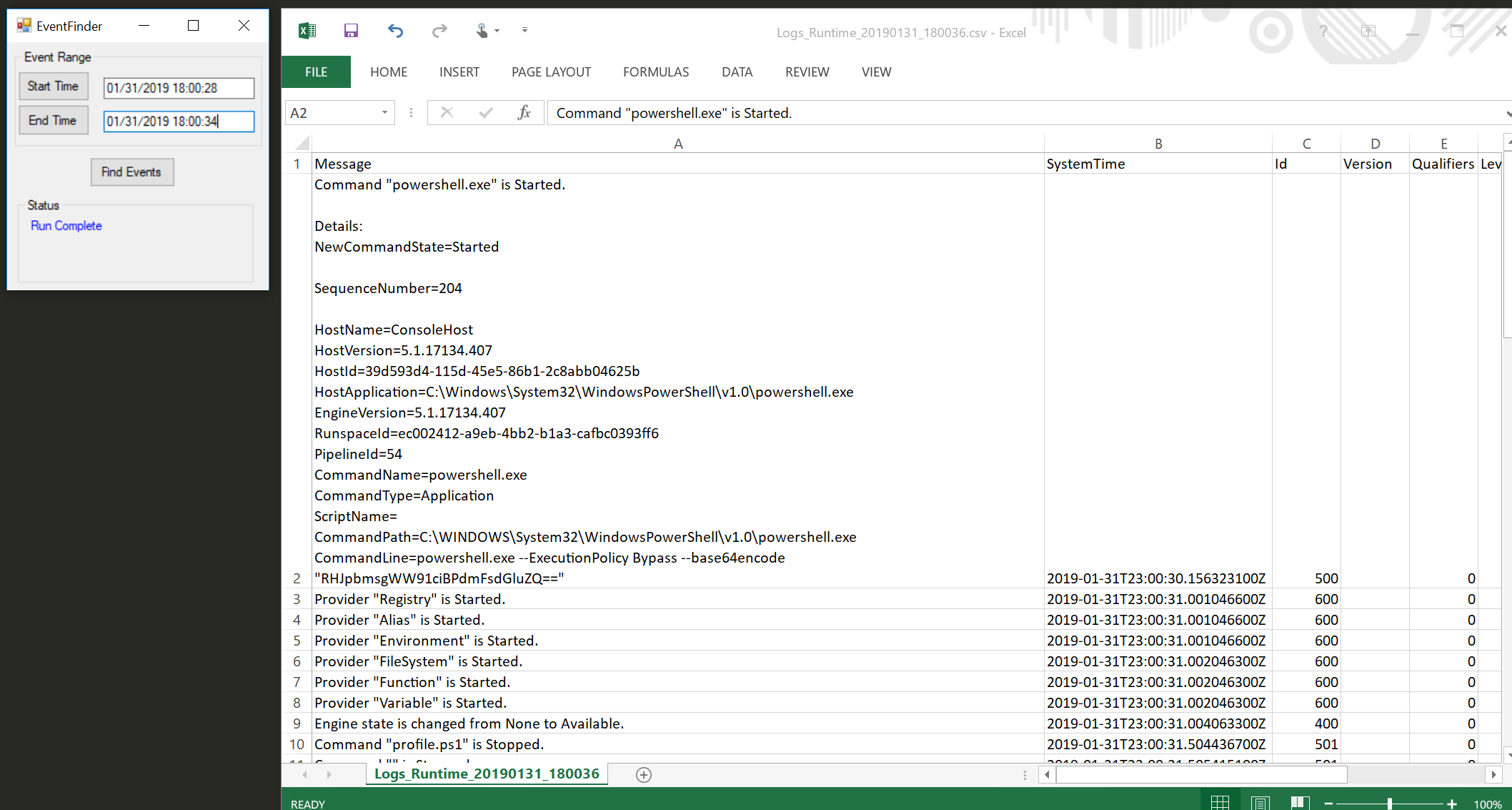
I created this with the SOC analyst/blue team/threat hunter maybe? in mind. That said, I think this would also be helpful for members of a support team. Basically, you start the program and click Start Time. Then do whatever it is that executes malware, crashes a program, etc. Lastly, click Stop Time and Find Events. The program will dump all events, from all logs (except possibly 2, check GitHub issues) to the desktop in a nice CSV, sorted by time. You can also manually change the start/end times. SCREENSHOT!
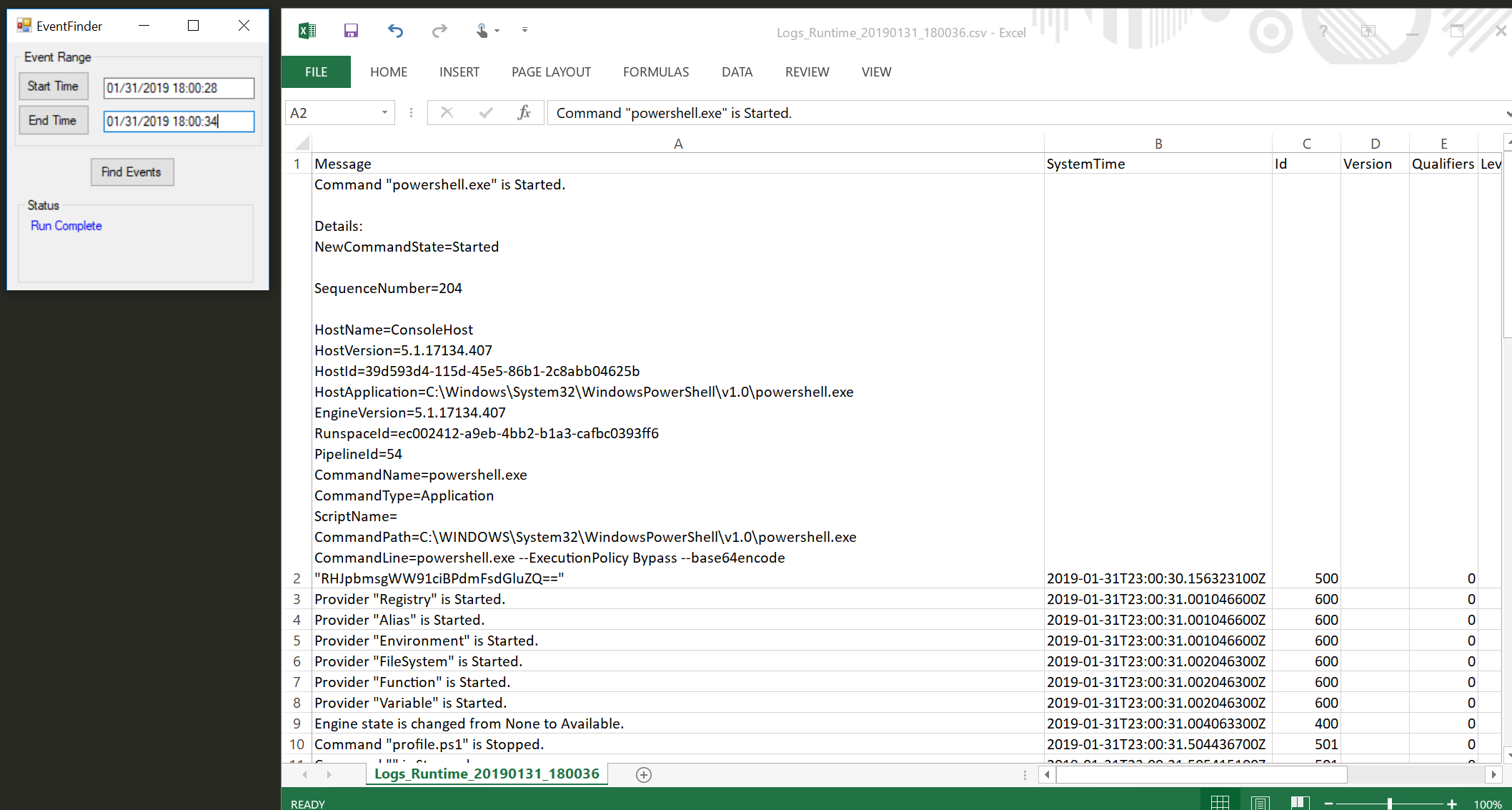
Why not just poke through the logs? There's a TON of stuff that's logged that most people don't think of. For example, RDP events. Everyone looks at Security, nobody pays attention to TerminalServices, or PowerShell, or any of the hundred of logs that are contained. This grew from an actual incident where an attacker cleared Security and absolutely nothing else. So yea, look at security, but look at it in the context of EVERYTHING ELSE that was created around it!
Background
I wrote a thing that, like all good things, was born out of a need. I wanted to find event logs caused by an action, but wasn't happy with my previous solution for a couple of reasons.
- Clearing logs isn't ideal. You could backup the event logs, but I would rather avoid that all together.
- It's noisy. I'm not concerned about this from the point of view of getting caught, it's my lab, but it makes identifying correct events harder.
- It's "messy". The output isn't neat, requires manual cleanup, is not in an ingestible format.
So I set out to make something better.
I started trying to find something that would just clear all the event logs at once, eliminating most of the noise (though there's still problems). Unfortunately, there really isn't anything. Malware Archaeology did pretty much the same thing I was doing, Log Parser didn't take wildcards.
I modified a little PowerShell GUI. My thought was that hopefully, since everything was contained in one script, it would only create a single event when run. This wasn't the case (as some of you probably already knew). It would create an event in both PowerShell logs each time it looped through and executed a section of the script, and then another as it looped through each event.
Still, I learned a lot, and if you want to review the code, you can check it out here: https://github.com/BeanBagKing/EventFinder
Enter C#
I've never written anything in C#, but I've been told that PowerShell translates well since they both leverage .NET. I'm still not sure this is the case, but as Mark Twain said, "To succeed in life, you need two things: ignorance and confidence", and I have to say, it turned out pretty well.
The end product does exactly what I want (as best as I can tell). It doesn't clutter up event logs a lot. Everything is logged of course, but we aren't clearing them in mass, nor are we running scripts in a loop. It gives me nice output, ordered and in CSV format.
Future
This works well enough for now. I do want to make it a bit neater (add an icon, better about page, etc.) and, at a minimum, make it read events from files so you can grab ranges from offline evidence. I also wouldn't mind fixing it to take in a few other log types, such as Windows Firewall. Really, that's the extent of it at this point, feel free to make suggestions either here, or on the GitHub Page.
Video Demonstration
Thanks to Richard Davis of 13cubed for a very professional demo of the tool!
